
bluetooth (bLE) Mesh for access control
Bluetooth mesh technology developed for smart lighting and other IoT applications can be adapted for other interesting use cases. Access control being one of them. Bluetooth is seemingly becoming a part of all access control hardware and using that to create a mesh network create a disruptive technology platform which changes the way access control systems are used and deployed.
Bluetooth mesh technology developed for smart lighting and other IoT applications can be adapted for other interesting use cases. Access control being one of them. Bluetooth is seemingly becoming a part of all access control hardware and using that to create a mesh network create a disruptive technology platform which changes the way access control systems are used and deployed.

Introduction
This article will introduce you to the concept of using BLE (Bluetooth Low Energy) Mesh technology for access control applications. Access control systems have been around for a few decades now. A normal person using an access control system takes things for granted, and expects that when he flashes his card on to an access control reader, the door just unlocks. What goes behind an access control system is a bunch of hardware and a network of cables running across buildings which ensures the system works all the time. This system has hardly changed over the last few decades. In the age of wireless communication, Wifi and IoT, access control systems still use legacy technologies. The new age access control solutions have started leveraging the smart phone as a credential but very little progress has been made on the networking side of access control. This article will put some light on how IoT is impacting access control systems and how the future will unfold for access control.
If you look back into history the first access control systems were in the form of lock and keys. Pre historic ages used complex set of keys and locks to ensure secure entry to barriers. In around 1950s and 1960s modern access control systems which allowed the use keypads to allow access to users. Users entered a unique key known only to the authorized users to gain access. This system provided almost no security but solved the problem of managing keys for the doors. Card readers came into existence to solve the problems faced by keypad-based access. Magnetic cards and readers became a very popular means of access control. This system gradually evolved into RFID based card readers which worked based on proximity. This is the system most of us are currently familiar with. One thing which remained constant throughout the evolution of access control systems was the Weigand interface which became popular in 1980s. Since then by far majority of the access control readers support the Weigand standard. IP door readers also became quite popular once LAN started getting utilized in offices. However, Wifi based access control readers never took-off for obvious reasons of poor security and reliability. An improved standard for access control networking called OSDP (Open Supervised Device Protocol) has started seeing adoption recently. OSDP addresses the security vulnerabilities of Weigand and also helps reduce the amount of wiring, thanks to its multi drop capability. The modern access control systems have evolved to a point where now other methods of authorizations are widely used. Mifare cards, Fingerprint IDs, Face recognition-based IDs and now the latest trend of smartphone credentials are being used as a means of access. Mobile based access control is one of the fastest growing trends in the market since 2012. We are now at a point where a radical shift in access control systems and technology is imminent.
I am sure by now some of you have started to wonder on the fact that if we are using Wifi (Wireless communication) to stream videos, or receive e-mails or do most of our work while in Office, why are these access control systems still using a wired networks for communication. That is exactly what we wondered at Spintly and resulted into we working towards building a wireless solution for access control. With the goal of getting rid of wires from access control systems various wireless technologies were evaluated. Wifi was the immediate first choice because of its ubiquitous nature. But quickly we realized that typically, Wifi networks in offices are maintained by the IT infrastructure department and cannot act as a reliable network for access control system. Wifi being an IP based system configuration of devices through firewalls posed challenges. Zigbee as a very strong candidate for a wireless access control network. Zigbee even supports mesh topology. But look at the way the market was moving Bluetooth was already being used as a credential to authenticate users. Now adding Zigbee hardware into each reader seemed like a dumb choice. Why use 2 wireless technologies in the same device and increase the cost of the readers. Just around 2017 the BLE (Bluetooth low energy) Mesh standard was getting defined. This created exciting opportunities for the access control world and Spintly was quick to jump onto this opportunity. Figure1 shows how BLE-Mesh has the potential to change the way access control systems are deployed and set-up. This is the age of IoT (Internet of Things) where every device or appliance we use or will use in future will have some form of connectivity embedded into it. Access control readers are devices which need to be connected to the internet and yet need to very secure. Thus, the choice of wireless connectivity used in access control readers is critical.
Bluetooth Mesh as a standard was announced by Bluetooth SIG in November-2017 and was mainly focused on Lighting applications. However, it was defined in such a way that a model layer was defined which allowed exchange of application specific messages. These allowed adopters to define custom models based on their use case. In this case these models could be used for access control use case. Some of the key features of Bluetooth and Bluetooth mesh which make it suitable for access control applications are listed below.
- Bluetooth is Ubiquitous: Bluetooth is one of the most widely used wireless technologies in the world. Bluetooth is present in your smartphone, every portable computing device, cars and Bluetooth headsets. This has resulted into high volume production of Bluetooth chips sets and which has driven their prices to a level that Bluetooth devices tend to be very cost effective. Bluetooth is already getting accepted as a very secure credential for access control and is already present in many access control readers and thus it just makes sense to use Bluetooth as a networking medium.
- Bluetooth Mesh is robust wireless standard: Bluetooth mesh uses BLE advertising signals. BLE advertising happens on channels which fall in the inter-band regions of the 2.4GHz (ISM) spectrum. Hence these signals are very less susceptible to effects of Noise caused by Wifi and Bluetooth Classic. This makes BLE mesh robust in presence of other 2.4GHz signals. Bluetooth mesh also has features like TTL (Time to live) and caching which ensures the messages take the optimum number of hops to reach their destination.
- Bluetooth mesh is highly secure: BLE mesh uses various levels of encryption using AES-128 bit encryption to secure the messages. This makes the network one of the most secure IoT networks for data communication.
- Bluetooth mesh is self-healing: Bluetooth mesh is self-healing in nature which means that it allows adding and removing of devices in the network on the go. Even if a device in the network goes down the network automatically reconfigures itself and the messages continue to flow without any down-time.
One can learn more about Bluetooth mesh by visiting the resources page on the Bluetooth website
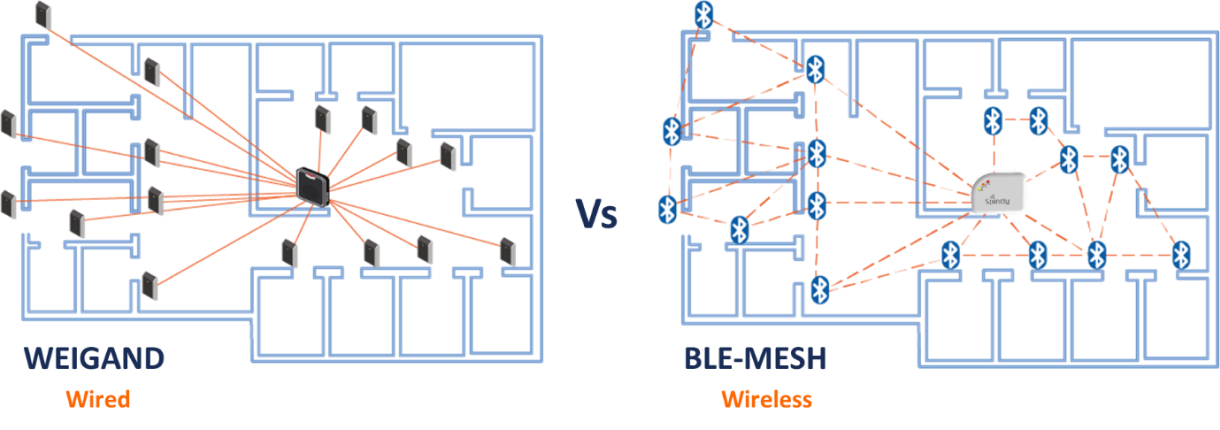
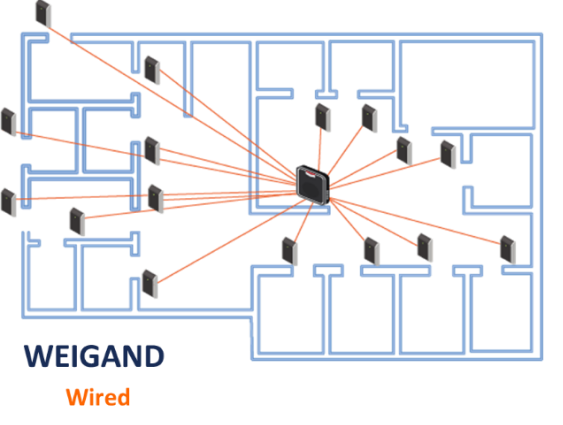

In conclusion, the future of access control is very exciting and is at a stage where a big shift in the way of doing things in the access control world is expected. Various standards and technologies will be proposed and experimented with. But Bluetooth seems to be front runner mainly due to the fact that companies like Silvair are already building a robust smart lighting networks using BLE-mesh and the ecosystem is shaping up towards an interoperable BLE mesh enabled smart buildings infrastructure.


