Security risks of Weigand
Wiegand Interface: Security Analysis
Wiegand technology is widely used in legacy access control systems and can be part of the card–reader interface, reader–controller interface, or a binary bit format itself which is sent between the card – reader – controller. The wired communication taking place between the reader and the controller is the central mechanism in the access card system. The Wiegand devices or the card basically stores the employee’s identification number which is picked up by Wiegand.
In this article, we’ll be talking specifically about the reader–controller interface and how easy it is to read and a data stream on those lines and deduce the credential information out of it. Although the communication interface being wired is perceived to be secure, we will show here how easy it is to read the card credentials and how using wired data transmission techniques for access control security systems is highly unsafe.
Wiegand Interface Basics
Wiegand is an asynchronous protocol and has 2 physical wired connections running from the reader to the controller as data lines.
Data 0 – This line is Active low and will indicate a 0 being sent to the controller
Data 1 – This line is also Active low and will indicate a 1 being sent to the controller.
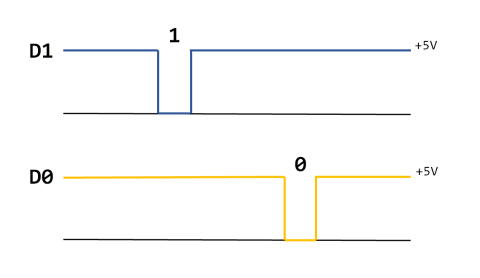
The HIGH here is 5V, but some interfaces can also have 12V as HIGH.
Reading the Card Data
For this, we have used a Mifare Classic 1KB card, but this will in general work for other card types as well. The user added in the system has the following card number
we probed the D0 and D1 lines of the interface using an Oscilloscope and got the following waveform.
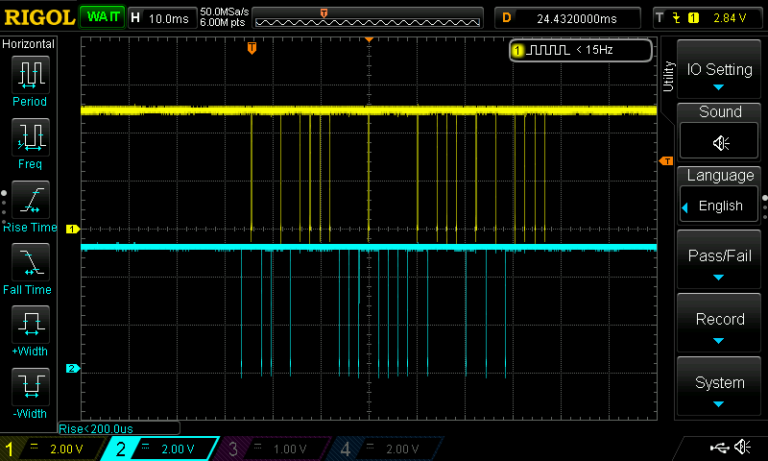
This is a zoomed-out snap of the entire transaction.
Yellow – Data 0
Blue – Data 1
As explained earlier both Data 0 and Data 1 will go low if a 0 or 1 is being sent respectively.
The bitstream is read from left to right and interpreted as:
10110100001110111101000101010000
Here we can note that the bitstream length is 32 bits.
Converting this to decimal gives us the following number:
3023819088
This number is the same as seen by the controller and saved as the credential ID of that user in the system.
Additionally, for Mifare cards, there is a UUID present for each card that is publicly visible. You can read the UUID by using a Smartphone or any other means. The card I used for this had the following UUID –
50:D1:3B:B4
This a 4-byte UUID in Hex format. Now if we look at the bitstream, we captured earlier and write it separating each byte –
10110100 00111011 11010001 01010000
Converting each byte to Hex we get –
B4 3B D1 50
This nothing but the UUID of the card, but in Little Endian Format.
Hence, we can see how the data is sent from Reader to the controller and how it can be easily decoded.
How wireless communication can be more secure

Secure Wireless Data Transmission
At Spintly we have adopted a fully wireless data transmission standard over a mesh protocol (BLE- mesh) where the readers communicate with each other and the Gateway over a wireless mesh communication protocol. This protocol uses encryption to secure the data which is sent over the air. Only the readers and Gateway have a required encryption key to make sense out of the data. This ensures full security of the data being exchanged. The highly powerful technology is the future of wireless access control systems.
In a Weigand Wired access control system, when you swipe your keycard or any access control device to unlock any door the Wiegand effect is taking place in the background and the security of such data transmission technique is prone to vulnerabilities.
BLE Mesh Wireless access control systems are highly secure and are also fast and easy to install. They reduce labor costs by eliminating wires and the need for hectic installations and updations.
This article shows how wired communication standards which are perceived to be secure are highly vulnerable and how wireless standards which are in general perceived to be insecure are much more secure and safe methods of transmitting data.


